HYKER Share
Securely store and share confidential information

With HYKER Share, you get an encrypted space, where you can create separate secure zones for different areas of operation, projects, or collaboration partners.
Each zone is isolated and meets high standards for information security, making it possible to store and share confidential information with both internal and external parties – without compromising control or integrity.
The solution is designed to support the Swedish total defense's requirements for secure information management.
Securely share information

Secure reception of documents from external parties
A government agency needed to receive confidential documents in an environment outside its usual cloud service. HYKER Share offered a secure platform with separate zones, encryption, BankID, and simple administration – all stored in Sweden and adapted to meet government requirements.
Secure sharing of classified information
A Swedish Utility company needed to handle sensitive information outside its standard IT environment in accordance with regulatory requirements. With HYKER Share, they received a separate, secure space with end-to-end encryption, BankID login, and comprehensive logging – enabling secure storage and sharing both internally and externally.
Secure handling of drawings for the defense industry
An industrial client with contracts in the defense sector needed to store and share drawings outside of their existing file management system. HYKER Share provided them with a secure environment with encryption, BankID, and traceability – in line with customers' requirements for secure information management.
Security based on end-to-end encryption
- End-to-end encryption
- Secure key management
- Swedish Data Center
End-to-end encryption (E2EE) means that the information is encrypted, in an unbroken chain, throughout its lifecycle. From the time a file is sent, received, stored, and all the way to the day the file is deleted. Another advantage is that we use Trusted Hardware (Intel SGX) to ensure the integrity of the distribution of public keys, so that a single public key server cannot compromise the security of the entire system. All information stored in HYKER's systems is stored under Swedish law in Swedish data centers and all systems are managed by security-classified personnel.
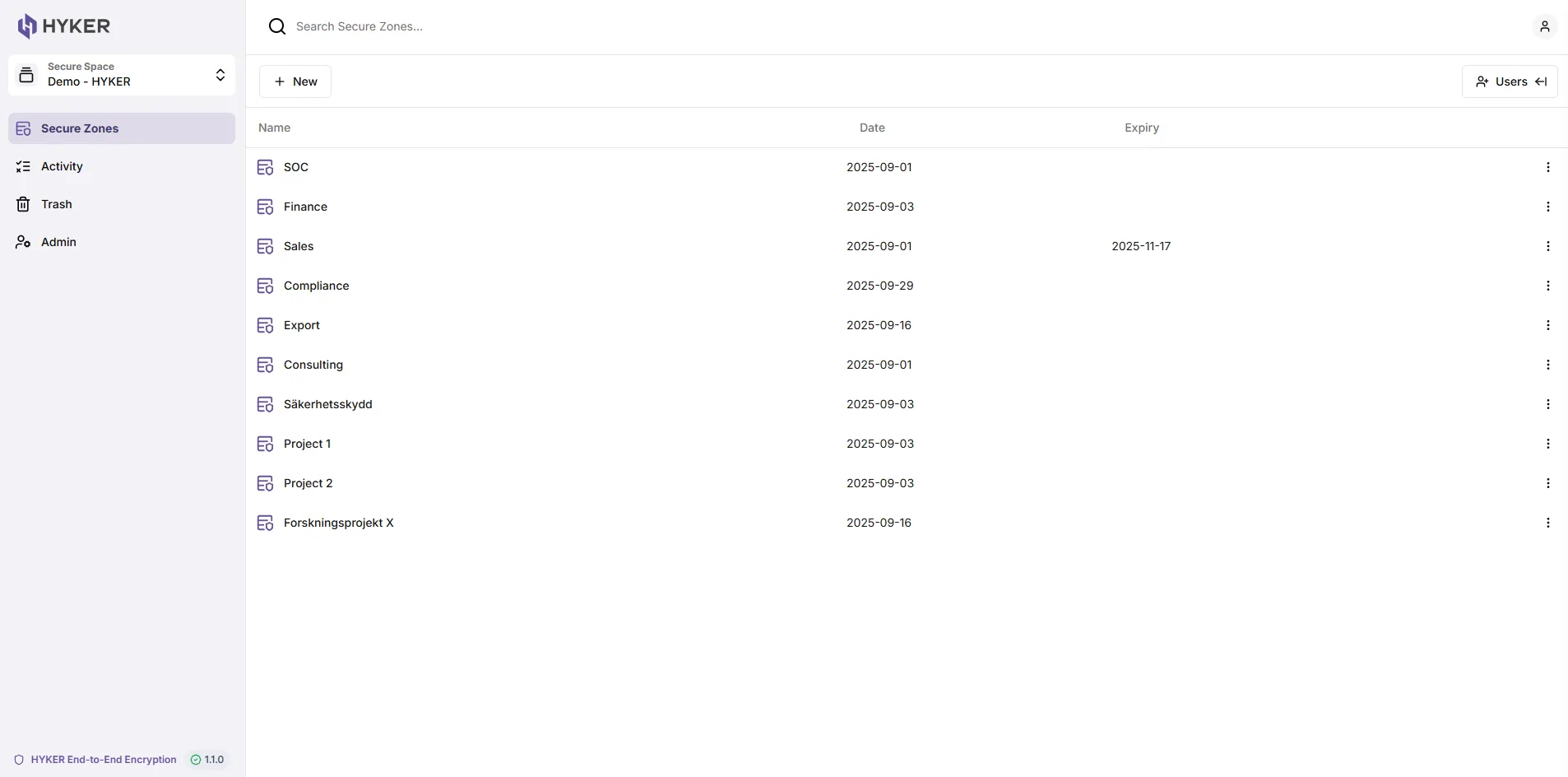
Easy to get started and use
- BankID
- No installation
- Computer and mobile-friendly
With HYKER Share, there’s no need to download software, configure settings, or train users to get started. The service is entirely web-based, allowing you to easily invite users who authenticate via BankID or two-factor authentication (no passwords allowed). You can customize permissions for both information and users, such as read-only access, upload/download privileges, and more.



