HYKER Security

It is a challenge to buy in and implement proper cybersecurity today. On the one hand, available technology for cybersecurity has lagged behind in technology development, technologies such as end-to-end encryption and hardware security are not standard in most companies. On the one hand, the security work is often done afterwards, when the systems are already in place. Security that is thought out after the fact and that is based on old techniques is both difficult to deal with and weak. HYKER delivers modern cybersecurity, which is easy to deal with and at the same time shuts out threats.
With HYKER, all communication is encrypted in an unbroken chain from sender to receiver without ever being exposed to third parties (not to HYKER as a system supplier either).
Key distribution is secured with trusted hardware in the form of Intel SGX, so clients are guaranteed to receive the correct cryptographic key material.
HYKER is a Swedish company and all storage of information takes place in Sweden, under Swedish law. We are constantly updated on new legislation and regulations for handling information at the confidentiality level, so that you as a customer can feel safe.
HYKER always puts cybersecurity first. That's why we only use the strongest tools, such as end-to-end encryption and trusted hardware. With these tools, we build systems so that unencrypted information is never ever handled by HYKER. Central servers also have no power to control the distribution of cryptographic keys, or to influence the log of system events. This way, your information won't leak even if a central server is the victim of a sophisticated attack.
Online information is valuable and vulnerable
If a breach occurs, you need a watertight last line of defense.
Insiders are involved in a significant percentage of all data breaches.
Your supply chain significantly increases your attack surface.
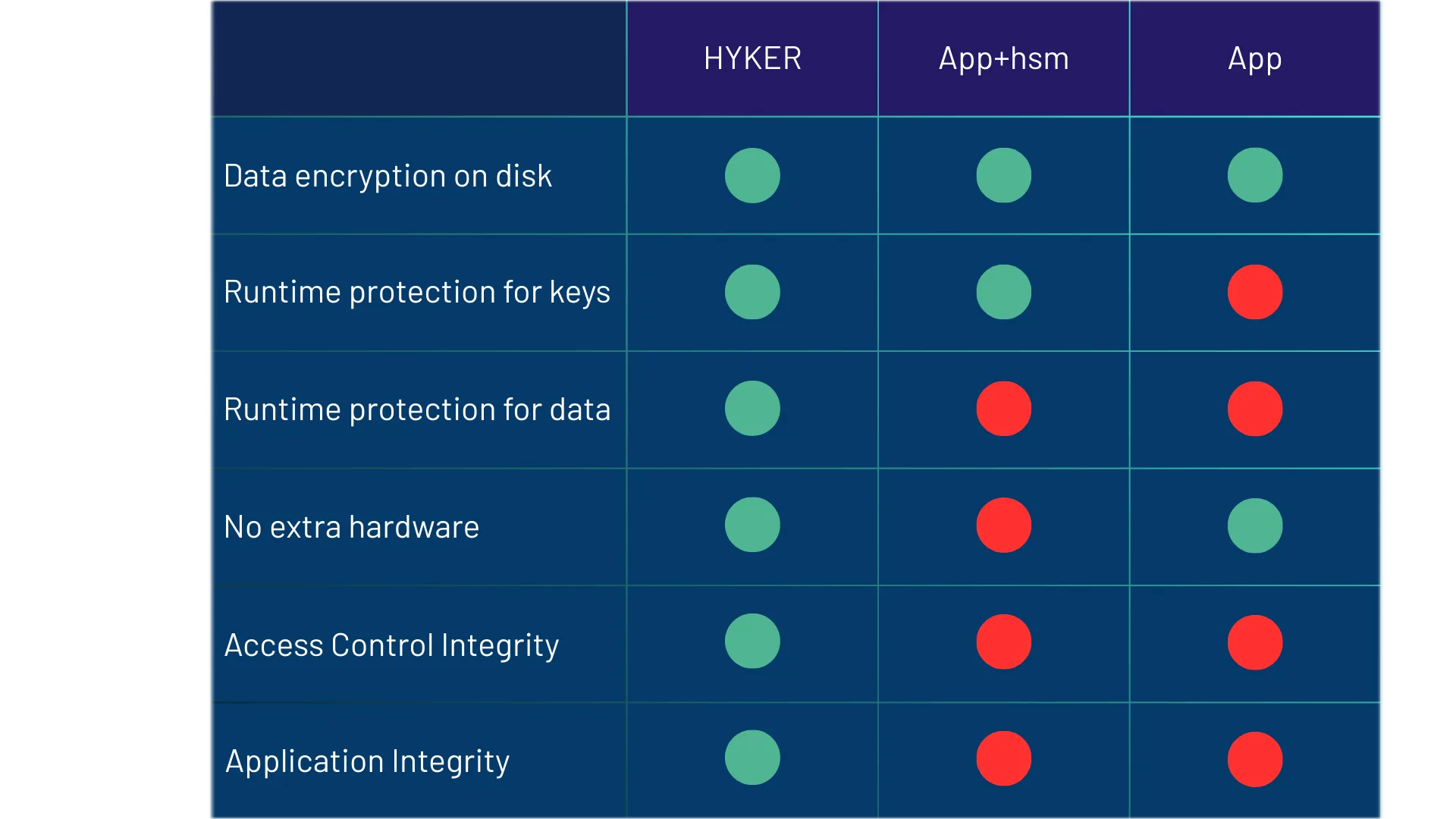
HYKER DBLP (Data Breach and Loss Protection)
The strongest protection available to protect information is encryption. Encrypted data is inaccessible to even the most sophisticated attacker. However, the fact that a system uses encryption should not be confused with the system as a whole being secure. Encryption is a technology that is part of a system, and must be applied with proper integrations according to secure design patterns.
For example, encryption must always be integrated with a key distribution system, which in turn must be integrated with a design pattern for access control and identity management. If this integration is not performed with security in focus, the security of the system is compromised.
Cybersecurity, at ease
Developing products that are both at the forefront of cybersecurity and user-friendly is a genuine challenge. At HYKER, we always take a holistic approach to security. We consider how each part affects security as a whole, and how it will impact the user experience. We can do this because we control all security-critical parts of our system and do not make security dependent on third parties such as infrastructure, hosting providers, etc. It takes a long time and requires extensive knowledge to develop systems in this way, but we do it because we prioritize security.


